Log In to Trezor Wallet | Trezor Login Guide Your Digital Assets
Managing your cryptocurrency portfolio starts with a secure login to your Trezor hardware wallet. Unlike typical web wallets, Trezor uses physical hardware devices combined with Trezor Suite app software to protect your private keys from online threats. This guide will walk you through the steps to log in securely, explaining core security concepts and troubleshooting common issues.
Your Trezor device makes it impossible for attackers to compromise your wallet remotely, as it requires physical confirmation of every transaction or action. The login process is streamlined for ease but does not sacrifice your security.
Step 1: Download and Install Trezor Suite
Begin by downloading the official Trezor Suite app from the trusted SatoshiLabs website. The Suite is available for Windows, macOS, Linux, and there’s even a web version accessible via supported browsers.
Using the official software guarantees you are using authentic code, which has been extensively audited and tested by the community.
- Visit the official site: trezor.io/start
- Select your platform and download the installer
- Run the installer and follow the prompts to complete setup
Remember that Trezor Suite does not require you to create a username or password. Instead, all security revolves around your physical hardware device and your recovery seed.
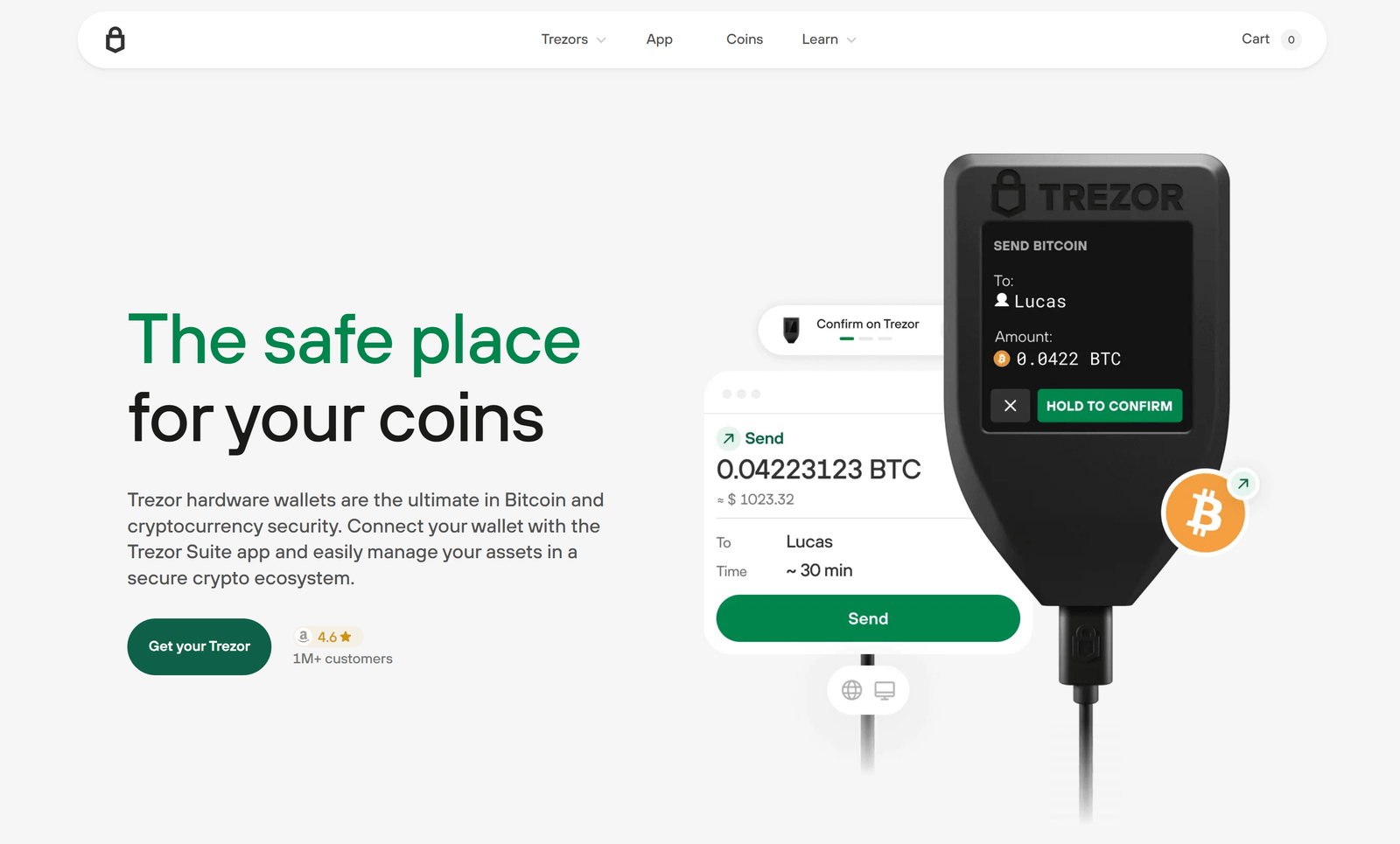
Step 2: Connect and Unlock Your Trezor Device
Connect your Trezor device to your computer using the supplied USB cable or via Bluetooth if your model supports it. The Suite will detect your device automatically.
If you are logging in for the first time, you will need to initialize your device or recover it from your seed phrase if you already own one.
Unlocking requires you to enter your PIN directly on the device screen — this keeps your PIN safe from malware on your computer.
- Follow the on-screen instructions on your device
- Enter your PIN securely using the device interface
- The Suite app will confirm successful login by displaying your wallet dashboard
Step 3: Confirm Device Authenticity
Before logging in, always verify the authenticity of your device. Trezor hardware wallets have built-in security features to ensure they are not tampered with.
- Check the holographic seal on the box is intact
- Review the Device Authenticity Check prompt in Trezor Suite
- If you notice any anomalies or warnings, contact official support immediately
This step protects you from counterfeit or compromised devices that can expose your assets.
Best Security Practices for Login
Secure login goes beyond just entering a PIN or connecting your device. Follow these important tips to keep your assets safe:
- Never enter your recovery seed anywhere but your hardware device
- Keep your recovery seed offline and stored safely
- Use a strong, unique PIN to protect your device
- Always update your Suite and firmware to the latest versions
- Connect your device only to trusted, secure computers
- Beware of phishing sites; access the official Trezor website directly
Troubleshooting Common Login Issues
Occasionally, users may encounter issues while attempting to log in. Here are solutions to frequent problems:
- Device Not Detected: Check your USB cable and port; try reconnecting or restarting the app.
- PIN Screen Not Appearing: Restart your Trezor device; ensure firmware is up to date.
- Connectivity Problems: Disable interfering software such as VPN or firewall temporarily.
- Lost Recovery Seed: If lost, your assets may be permanently inaccessible — secure your seed carefully.
Why Trezor Login is Superior to Software Wallets
Unlike software wallets that store keys on your computer or online, Trezor hardware wallets keep keys isolated in the device. This reduces risks of hacks, malware, or phishing attempted during login.
The login process requires physical confirmation and keeps your personal credentials off any internet-connected device, delivering unparalleled security for your cryptocurrencies.
Staying Informed and Getting Support
For any login troubles or security questions, use official support channels and community forums. Keeping your software and firmware updated ensures you benefit from the latest security enhancements.
Join the Trezor community to learn best practices and stay ahead of potential cyber threats.